3-2-1 Backup Strategy Guide
The 3-2-1 backup rule is a widely adopted, flexible framework for protecting data in almost any contingency. Simply put, the 3-2-1 backup rule is:
3 – Save 3 copies of your data
2 – On 2 different media types
1 – With 1 copy saved off-site
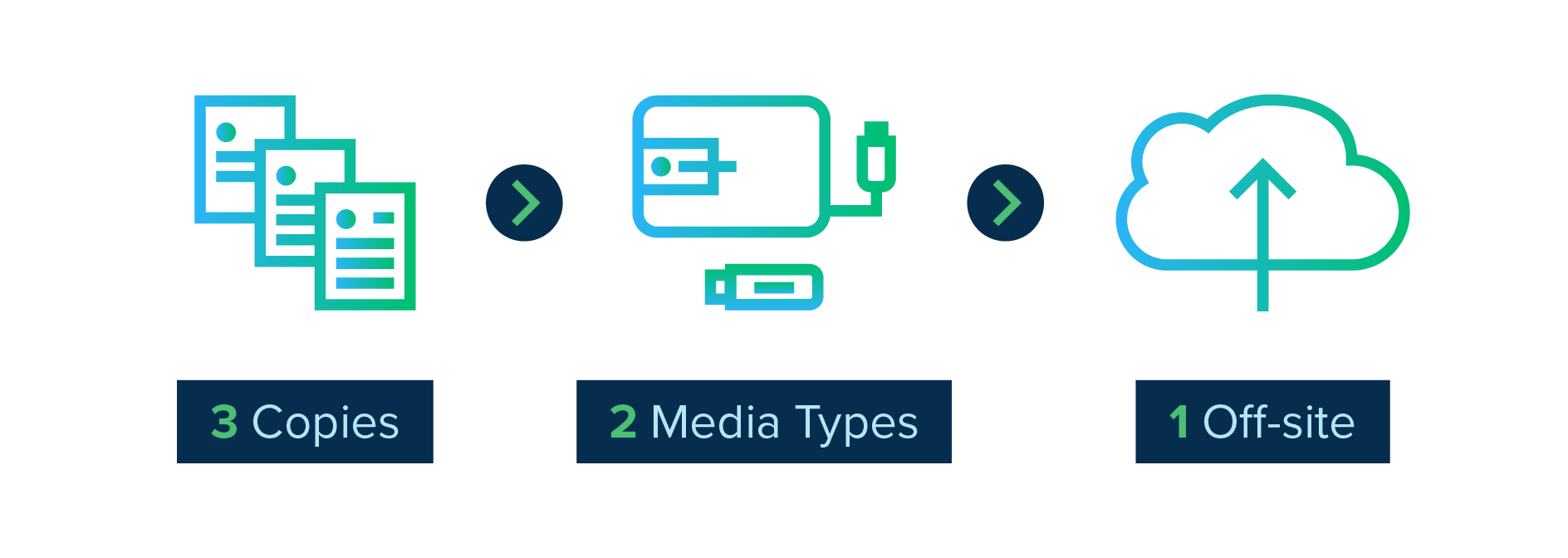
The rule was first coined in photographer Peter Krogh’s 2005 book on digital asset management. Over time, people have adapted it to suit a changing business and technical landscape, but the core concepts remain the same. In this guide, we’ll explore some nuances of the 3-2-1 backup rule and help you identify why and how to apply it to your unique situation.
Contents
Why companies need 3-2-1 plans: biggest data-loss threats
- Ransomware
- User Error
- Natural disasters
Components of a 3-2-1 backup system
- Local files
- Network drive folder
- External drive
- Dedicated cloud-based backup
3-2-1 backup best practices in 2022 and beyond
- Consider RTO (Restore Time Objective)
- Support your business continuity plan
- Remember that humans are human
- Evaluate adding another “1” to your backup plan
Disaster-proof your data
Why companies need 3-2-1 plans: biggest data-loss threats
While humankind will never tame all the natural disasters, snare every hacker, or create an un-losable laptop, what we can do is have a plan. A 3-2-1 data backup strategy provides comprehensive data loss protection from threats that would drastically affect a business’s bottom line.
The first step, as the saying goes, is to “know thy enemy.” And in the case of data protection, that means understanding your most likely causes of data loss. For most businesses, they fall into three categories: ransomware, user error, and natural disasters.
Ransomware
Ransomware is a form of malicious software (malware) that hijacks your data and holds it hostage until you pay a fee to the perpetrators. Many businesses think they don’t have anything of value for a cybercriminal so they don’t put time or resources toward protecting themselves. Cybercriminals, on the other hand, can always find something of value in any organization. Even if you don’t believe you have particularly sensitive or proprietary information, bad actors can still wreak havoc on operations by preventing access to vital systems and/or exfiltrating data for their own later use or sale.
Verizon’s 2022 Data Breach Investigations Report includes a number of alarming statistics about ransomware:
- Almost 70% of malware breaches come in the form of ransomware
- That number rises to around 80% for small businesses
- Ransomware attacks were up 13% in 2022 – more than in the last 5 years combined
Regardless of the reason they were targeted, a business locked out of its data has no guarantee that making a cryptocurrency payment to an anonymous address will result in them getting their data back. This is one reason cybercrime experts recommend victims don’t pay a ransom. The FBI advises that “paying a ransom doesn’t guarantee you or your organization will get any data back. It also encourages perpetrators to target more victims and offers an incentive for others to get involved in this type of illegal activity.”
When ransomware strikes, the damage is already done. Therefore, having secure backups of important data gives power back to business owners and prevents them from needlessly incentivizing cybercrime.
Related reading: How to prevent ransomware attacks on your business

The FBI advises that paying a ransom doesn’t guarantee you or your organization will get any data back.
And paying a ransom offers an incentive for others to get involved in this type of illegal activity
User Error
Whether a user accidentally deletes something important, their hardware gives up the ghost, or a laptop gets left on the subway, data loss can have serious productivity and brand impacts to a business. Trying to recreate that nearly-finished slide deck or customer project is both frustrating and presents opportunity cost in the way of new work being completed. Additionally, there can be far more serious consequences when important intellectual property is lost or customer data is compromised. Imagine the financial impact to the world’s leading soda brand if their secret recipe was deleted. These scenarios seriously damage reputations, and trust, and business continuity.
While we can’t always protect users from these unfortunate occurrences, backing up user data without getting in the user’s way significantly minimizes the negative repercussions.
Natural Disasters
According to FEMA, around 25% of businesses close their doors after a natural disaster. While desks and chairs can be readily replaced by insurance, destruction of important data like customer lists, financial information, product roadmaps, and intellectual property is much harder to recover from.
Many businesses keep their backups on external drives or an on-premises server. Unfortunately, this lack of geographical redundancy leaves both the original data and the on-site backups vulnerable to any location-based disaster.
With a 3-2-1 data backup strategy, you have 3 copies of data, backed up to local and cloud locations to ensure you always have valuable data accessible to restore from regardless of natural disasters.
Components of a 3-2-1 backup system
The user’s working files are the first of the 3 copies of their data. Users today work on files saved locally on their computer, over VPN on a company server, within a cloud service like Google Docs, and often a combination of these.
Many users assume that files stored in sync-and-share solutions like Dropbox and OneDrive don’t have to be backed up since they’re already in the cloud. These systems are excellent for collaboration and sharing between devices and have become more useful than ever since Covid-19 accelerated the trend toward remote and hybrid work. However, these solutions are not a substitute for backup. They only store a single (albeit secured from site-disaster) copy of working data, which is shared across all devices. A change to one, such as in the case of ransomware, will propagate to all.
Network drive folder (usually on an on-premises server)
At many organizations, company policy dictates users should place their data into a network folder hosted on a company owned server. That server then gets automatically backed up, often to yet another on-premises server.
Network storage is easy enough to use, is well understood in the industry, and server backups can be automated. These are all great reasons to include network file storage in your backup architecture. But there are several reasons it’s not a stand-alone solution:
- It requires access to the network – usually via VPN.
- Often, users forget (or willfully refuse) to put their documents on the server or into the correct folder.
- In addition, onsite network drives are subject to the same location-based risks – theft, natural disasters, leaky water pipes, etc. – as the endpoints they’re protecting.
External drive (storage devices attached to the endpoints or servers)
This solution offers ready access to your data and can often be automated. External drives have become smaller, cheaper, and higher capacity over the years, and they’re also a great option for portability.
There are some cons, however. External drives attached to endpoints are a great solution for individuals or even small teams, but they don’t scale when it comes to monitoring them for integrity, capacity, and compliance. This presents a significant barrier in a remote-first world. Drives attached locally to a machine, while presenting a control against simple hardware failure, are still subject to the same user behavior and location-based risks as a network drive.
Dedicated cloud-based backup
An automated solution to keep a copy of end-user data in the cloud which can help protect against cybercrimes, human error, and provide critical geographic redundancy.
Automatic cloud backups happen continuously in the background and require no user action, which means that data loss can be limited to whenever the last backup was. Because restoring this data requires downloading files from the cloud, you must be connected to the internet in order to access them.
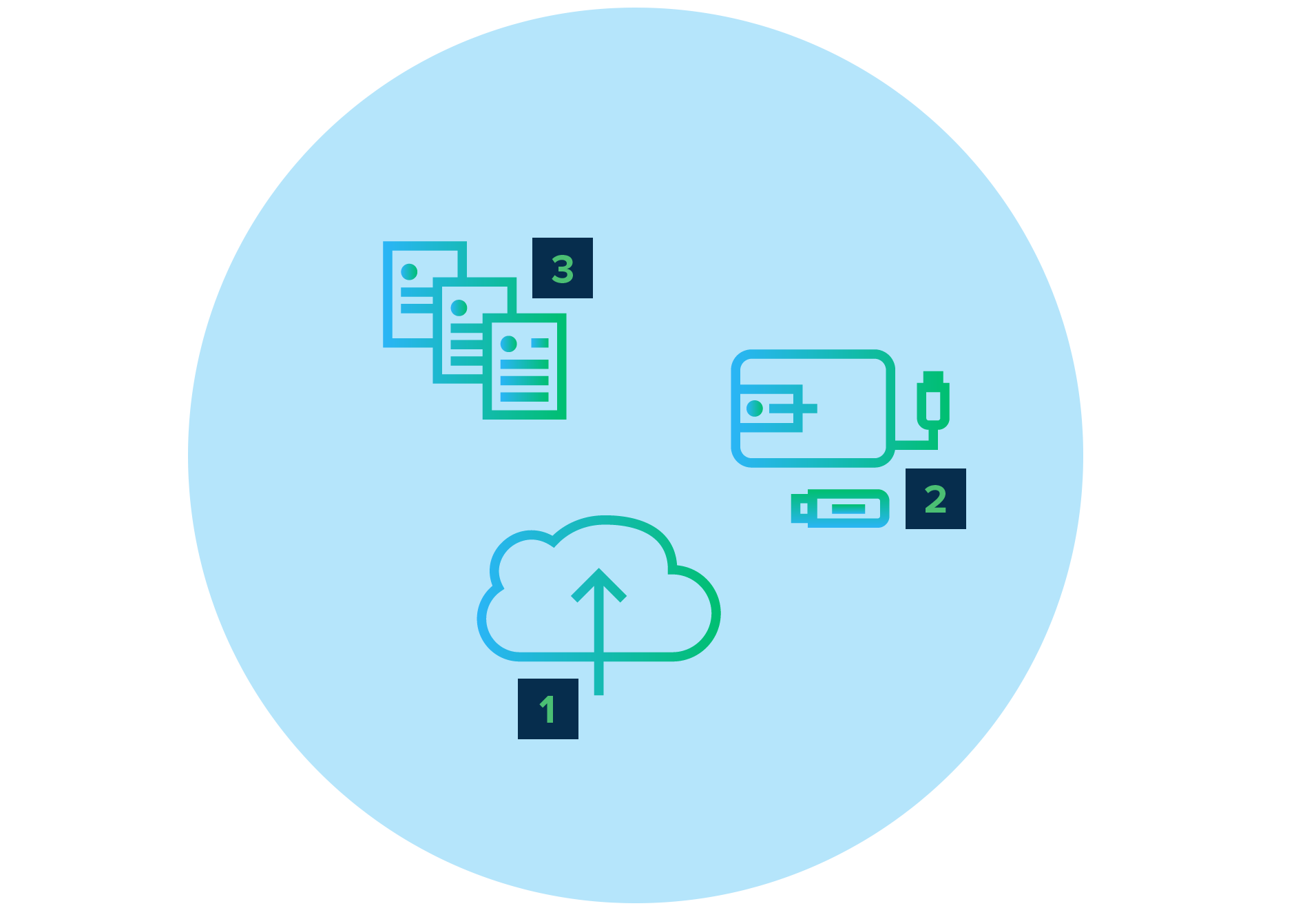
None of these systems present a silver bullet alone, but when layered together in a way that doesn’t hamper end-user productivity
they each work together to protect against the blight of data-loss
3-2-1 backup best practices in 2022 and beyond
A lot has changed since 3-2-1 backup was coined in 2005. While the core concept remains relevant, there are additional considerations you should be thinking about as you visit (or revisit) this approach in your own organization.
Consider RTO (Restore Time Objective)
For endpoint users, at least one of your backup copies should prioritize RTO (Restore Time Objective). In the event of data loss, you want users to get back to work as quickly as possible. After all, we’re not backing up data simply for the sake of backing up data. Employee productivity has a serious impact on your business operations.
Consider a backup solution that allows users to easily perform their own restores – either of specific files or larger data sets. Additionally, consider a solution which allows for copies to be stored in multiple locations (both in the cloud and local to the device) and administered centrally. This frees up your IT team while reducing RTO. Also consider how frequently you’re backing up your data and what data retention policies make the most sense for you.
Related reading: Protect your small business from downtime
Support your business continuity plan
A great resource to begin delving into business continuity plans is ready.gov. A key element of planning for business continuity is “to identify time-sensitive or critical business functions and processes and the resources that support them.”
Be absolutely sure that you’re properly backing up the files that are essential to your most critical business processes – and test those backups regularly to make sure they’re still running correctly.
You’ll also want to evaluate your data retention policies. Different organizations will have different data retention needs. If you work in a highly regulated industry, you will likely need to retain your data for far longer than other companies. And in the event of litigation, companies may have to preserve their data in a legal hold for a period of time. You don’t want to be scrambling to develop a process for this if an unfortunate legal situation suddenly arises.
Related reading: Complete guide to data loss protection
Be absolutely sure that you’re properly backing up the files that are essential to your most critical business processes
And test those backups regularly to make sure they’re still running correctly
Remember that humans are human
Far too many businesses rely on users to backup their own data in whatever way they see fit. It’s all well and good to trust your users, but humans are fallible. Lost, stolen, or broken computers, overwritten files, or accidental deletions happen to the best of us. And even savvy users can fall prey to ransomware and other malware.
Automating and systematizing your backup processes means you’re not relying on humans to act like machines. It protects your business’s intellectual property and customer data from human error. And it allows your employees to focus on what they do best – their own jobs.
Evaluate adding another “1” to your backup plan
To help bolster their cybersecurity, many organizations are now incorporating air-gapped and immutable backups of their data. This approach adds another “1” to the end of the 3-2-1 approach. In other words: 3 copies in 2 media types, with 1 offsite and 1 air-gapped or immutable copy.
Air-gapped backups
An air-gapped backup is simply a copy of your data on a device that has no connection to the internet. This may be accomplished using physical media like a tape drive. One disadvantage of this approach is increased RPO (Restore Point Objective). Restoring from physical media – especially if it’s stored off-site – can be a slower process than restoring from an internet-accessible location. An air-gapped backup may also not be necessary if you have an immutable backup.
Immutable backups
Another approach to the additional “1” is to ensure that at least one copy of your data is immutable. Immutable data may be connected to the internet – thus is not considered air-gapped – but is stored in such a way that it cannot be modified or deleted. Cloud backup solutions with end-to-end data encryption create immutable backups by encrypting your data on the endpoint before sending it to the cloud. And restored files are sent back to the endpoint encrypted and then decrypted locally. This insulates the rest of your organization from ransomware if one unfortunate employee’s machine is infected.

Disaster-proof your data
Nobody likes to think about worst case scenarios, but taking the time to create a 3-2-1 backup plan before there’s a disaster means you’ll be in a great position to weather any data loss storm.
An end-to-end encrypted cloud backup solution like CrashPlan can be a key element in your 3-2-1 backup system. Ready to give it a try? Sign up for a free 14-day trial and see for yourself.